- what is the best mobile monitoring program Google Pixel 3.
- Microphone Test.
- call tracker application for Oppo.
- mobile listening program Samsung.
- top mobile location software Galaxy Note.
- do you know if you’re phone has been breached?.
- how to set up mobile phone track Apple.
Aggressive Wi-Fi to cellular handover: When the signal is low, makes Wi-Fi more efficient in handing over the data connection to a cellular network. Input Figure 6.
Configure on-device developer options
Pointer location. Enable Show taps to display taps when you touch the screen. A circle appears under your finger or stylus and follows you as you move around the screen. A tap works like a pointer when you Record a video on your device. Enable Pointer Location to show the pointer tap location on the device with cross-hairs. A bar appears across the top of the screen to track the cross-hair coordinates figure 6. As you move the pointer, the coordinates in the bar track the cross-hair location and the pointer path draws on the screen.
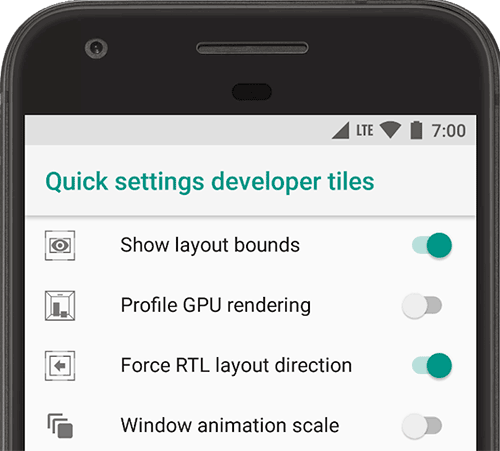
Enable Show Layout Bounds to show your app's clip bounds, margins, and other user interface constructions on the device, as shown in figure 7. Hardware accelerated rendering options provide ways to optimize your app for its target hardware platforms by leveraging hardware-based options such as the GPU, hardware layers, and multisample anti-aliasing MSAA. Tap Simulate color space to change the color scheme of the entire device UI.
The options refer to types of color blindness.
Have hackers tapped your phone? - Panda Security
Choices are Disabled no simulated color scheme , Monochromacy black, white, and gray , Deuteranomaly red-green , Protanomaly red-green , and Tritanomaly blue-yellow. Protanomaly refers to red-green color blindness with weakness in red colors, and Deuteranomaly shown in figure 8 refers to red-green color blindness with weakness in green colors. Debug GPU overdraw: Displays color-coding on your device so you can visualize how how many times the same pixel has been drawn in the same frame. The visualization shows where your app might be doing more rendering than necessary.
For more information, see Visualize GPU overdraw.
Debug non-rectangular clip operations: Turns off the clipping area on the canvas to create unusual non-rectangular canvas areas. Normally, the clipping area prevents drawing anything outside the bounds of the circular clipping area. Disable HW overlays: Using the hardware overlay enables each app that displays something on the screen to use less processing power.
What Our Satisfied Customers Have to Say About Us
Without the overlay, an app shares the video memory and has to constantly check for collision and clipping to render a proper image. The checking uses a lot of processing power. Media Figure 9. Bar representation. Automatic routing can interfere with apps that are USB-aware. Monitoring options provide visual information about app performance, such as long thread and GPU operations. For more information, see Profile GPU rendering. Tap Background process limit to set the number of processes that can run in the background at one time.
Possible settings are shown in figure Tap Reset ShortcutManager rate-limiting during testing so background apps can continue to call shortcut APIs until the rate limit is reached again.
For more information about shortcuts and rate limits, see ShortcutManager. Enable Don't keep activities to increase battery life by destroying every activity as soon as the user leaves the activity's main view. Content and code samples on this page are subject to the licenses described in the Content License.
Android Studio. Download What's new User guide Preview. Meet Android Studio. Manage your project. Write your app. Build and run your app. Run apps on the emulator. Run apps on a hardware device. Configure your build.
Debug your app. Profits from advertising can be considerably increased through effective targeting, which requires the collection of detailed personal information [ 68 ]. There is no doubt that smartphone sensor data can be very useful for this purpose. The widespread use of smartphones makes them a particularly attractive hacking target [ 4 ].
Not only cyber criminals, but also law enforcement agencies and secret services invest heavily in their capabilities to exploit software flaws and other security vulnerabilities in consumer electronics [ 73 ]. With the help of specialized tools, smartphone microphones can even be tapped when the device is or seems switched off [ 73 ]. Such attacks can also be successful in high-security environments.
In a recent case, for example, more than Israeli servicemen had their phones infected with spyware that allowed unknown adversaries to control built-in cameras and microphones [ 57 ]. Besides the United States and some European nations, other developed countries, such as Russia, Israel and China, also have highly sophisticated spying technology at their disposal [ 75 ]. Less developed countries and other actors can buy digital eavesdropping tools from a flourishing industry of surveillance contractors at comparatively low prices [ 60 ].
Eavesdropping capabilities of criminal organizations should not be underestimated, either. So far, despite significant research efforts, no evidence has been found to confirm the widespread suspicion that firms are secretly eavesdropping on smartphone users to inform ads. To the best of our knowledge, however, the opposite has not been proven either. While some threat scenarios e. In comparison with the researchers cited in this paper, it can be assumed that certain companies have significantly more financial resources, more training data, and more technical expertise in areas such as signal processing, data compression, covert channels, and automatic speech recognition.
This is — besides unresolved contradictions between cited studies and large remaining research gaps — another reason why existing work should not be seen as final and conclusive, but rather as an initial exploration of the issue. While this paper focuses on smartphones, it should be noted that microphones and motion sensors are also present in a variety of other Internet-connected devices, including not only VR headsets, wearable fitness trackers and smartwatches, but also baby monitors, toys, remote controls, cars, household appliances, laptops, and smart speakers.
Some of these devices may have weaker privacy safeguards than smartphones. For instance, they may not ask for user permission before turning on the microphone or may not impose a limit on sensor sampling frequencies. Numerous devices, including smart TVs [ 13 ], smart speakers [ 27 ], and connected toys [ 26 ], have already been suspected to spy on private conversations of their users. Certain smart home devices, such as home security alarms, may even contain a hidden microphone without disclosing it in the product specifications [ 44 ].
For these reasons, it is essential to also thoroughly examine non-smartphone devices when investigating suspicions of eavesdropping. It is quite possible, at the same time, that the fears of advertising companies eavesdropping on private conversations are unfounded. Besides the widespread attribution to chance, one alternative approach to explaining strangely accurate advertisements points to all the established tracking technologies commonly employed by advertisers that do not depend on any phone sensors or microphones [ 51 ].
Although their own search engines, social networks, email services, route planners, instant messengers, and media platforms already give them intimate insight into the lives of billions of people, advertising giants like Facebook and Google also intensively track user behavior on foreign websites and apps. Of the Through their analytics services and like buttons, Google and Facebook can track clicks and scrolls of Internet users on a vast number of websites [ 17 ].
The deep and potentially unexpected insights that result from such ubiquitous surveillance can be used for micro-targeted advertising and might thereby create an illusion of being eavesdropped upon, especially if the data subject is ill-informed about the pervasiveness and impressive possibilities of data linkage. Even without being used for audio snooping, smartphones in their current configuration allow a large variety of actors to track private citizen in a much more efficient and detailed way than would ever have been possible in even the most repressive regimes and police states of the 20th century.
